Bad Timer!
Posted: September 15, 2011 | Author: simeshev | Filed under: Java | Leave a comment »java.util.Timer has a possibility of a memory leak. Here is how to fix it.
java.util.Timer provides an concise API for scheduling tasks in Java. TimerTask is an interface that is used to implement the scheduled work.
TimerTask has a method cancel() that is supposed to cancel a task previously scheduled for execution by the timer. Here is what Javadoc for TimerTask.cancel() says:
/**
* Cancels this timer task. If the task has been scheduled for one-time
* execution and has not yet run, or has not yet been scheduled, it will
* never run. If the task has been scheduled for repeated execution, it
* will never run again. (If the task is running when this call occurs,
* the task will run to completion, but will never run again.)
*/
public boolean cancel();
Yet, the following innocent code fragment will cause OutOfMemoryError in just a few moments:
class MyTask extends TimerTask {
public void run() {
// Do nothing for the example purposes
}
}
...
Timer timer = new Timer();
...
for (int i = 0; i < 10000000; i++) {
final MyTask task = new MyTask();
timer.schedule(task, 30000);
task.cancel();
}
You may assume that, per documentation, canceling the task will completely remove it from the internal Timer structures. Unfortunately, this is not what happens in real life. What TimerTask.cancel() does is that it just marks the task as canceled. The actual removal occurs only when the timer executes a next scheduled task. If you have a lot of cancellations, and the next task is scheduled to run far in the future, this may cause OutOfMemoryError because all those canceled tasks will still be sitting in timer’s queue.
The simplest solution is to call Timer.purge() after each call to TimerTask.cancel(). This will force the timer to immediately remove canceled tasks from the timer queue:
...
Timer timer = new Timer();
...
for (int i = 0; i < 10000000; i++) {
final MyTask task = new MyTask();
timer.schedule(task, 30000);
task.cancel();
timer.purge();
}
Hope this helps.
Regards,
Slava Imeshev
Cacheonix | Clustered Java Cache
A SpecialTeas.com Relacement
Posted: September 11, 2011 | Author: simeshev | Filed under: General | Leave a comment »I have found a decent replacement for SpecialTeas.com. It’s Upton Teas Imports.
So, SpecialTeas.com went under which was a family micro-tragedy. After searching for awhile, I have found a decent replacement for SpecialTeas.com. It is Upton Tea Imports [1]. The most important thing is that the selection is very good and on par with SpecialTeas.com. The shipment is pretty fast. The tea is packaged well, and the samples are coming in tins:
We are happy campers again.
References
SCI-FI Movies That Will Blow Your Mind
Posted: September 4, 2011 | Author: simeshev | Filed under: General | Leave a comment »There is something in the makeup in software people’s brain that makes them love SCI-FI. Here are SCI-FI movies that I am sure you’ll love.
After having my mind blown twice in a row recently I thought it would benefit many if I logged those awesome SCI-FI movies so that you can enjoy them, too. I intend to keep this list growing. Here they go, in no particular order:
- Sunshine
- Lathe of Haven
- Absolon
- Alien
- Aliens
- Dark City
- Blade Runner
- Screamers
- Metropia
- Cypher
Regards,
Slava Imeshev
Presenting on Best Practices for Scaling Java Applications with Distributed Caching at Silicon Valley Code Camp
Posted: September 3, 2011 | Author: simeshev | Filed under: General | Leave a comment »I will be giving a talk on best practices for scaling Java applications with distributed caching on October 8 or 9, 2011 at Silicon Valley Code Camp.
This vendor-neutral session will explore ways for improving reliability, scalability, performance and concurrency of Java applications through local and distributed caching. You will learn how to identify data best fit for caching; deepen your knowledge with best practices for caching; understand distributed caching and ways it enables scalability of Java applications. We will discuss common usage scenarios for distributed caching and will provide best practices for the supporting network infrastructure.
Register here, it’s completely free: http://www.siliconvalley-codecamp.com/Sessions.aspx?ForceSortBySessionTime=true&AttendeeId=169
I will post the slides online after the session. If you cannot make it to Code Camp but want to get notified when the slides are available, drop me a line at simeshev@cacheonix.com.
See you there!
Regards,
Slava Imeshev
Moving from MS Outlook to Entourage Made Easy
Posted: August 23, 2011 | Author: simeshev | Filed under: General | Leave a comment »Moving from Outlook to Entourage is trivial and takes 15 minutes when you know what software to use. Here is how.
I switched from Windows to Mac OS X awhile ago, and one thing that really delayed completing the switch was moving contacts and a large message database from Outlook to Entourage. I googled “free outlook entourage” and wasted a few hours trying various 50-step suggestions that didn’t work. The bitch was “free” in my search query. At some point I decided that it just wasn’t worth my time and killed “free”.
In 5 minutes I found MessageSave by TechHit. It is worth every penny I’ve spent on it. With MessageSave my migration from Outlook to Entourage took around 15 minutes, attachments preserved. What message MessageSave does, it converts the proprietary Outlook message database to a set of Mbox-compatible files that Entourage understands. Here is a screenshot of the start screen:
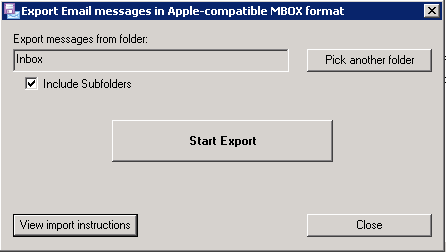
All you need after MessageSave completed the export is to copy those Mbox files to your Mac and drag’n’drop them into Entourage. Entourage will chew through them and you are done. MessageSave also allows to move your Outlook contacts and schedule. TechHit provides a detailed step-by-step manual on how to import Mbox files into Entourage.
One thing to remember is that exporting to the same folder twice will produce duplicate messages on import. Make sure you are exporting your messages to a clean folder.
Hope this saves you a few gray hairs.
iPhone Case Awesomeness
Posted: July 26, 2011 | Author: simeshev | Filed under: Hardware | Leave a comment »Today, I have dropped my iPhone on a hard surface for the first time. This went completely uneventful because smart me had it enclosed in a hard case. I’m using Incase’s Slider Case for my iPhone 4 and I’ve been using Incase since my first iPhone and I think Incase makes best iPhone cases.
OS X: Disabling Front Row Keyboard Shortcut
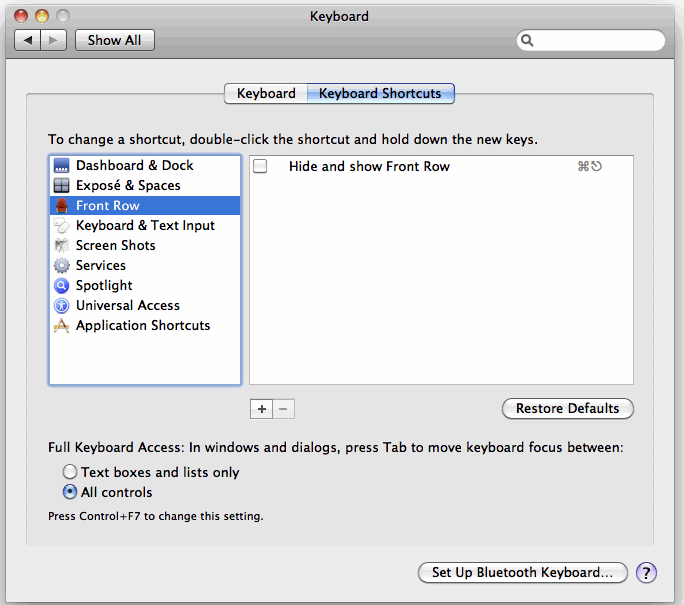
Posted: July 6, 2011 | Author: simeshev | Filed under: OS X | Leave a comment »Front Row tends to pop up unexpectedly while I am coding which is very annoying because it breaks my thought flow. The good news it’s very easy to disable the keyboard shortcut that causes this. Here is how.
- Go to System Preferences.
- Go to Keyboard Shortcuts.
- Click on Front Row.
- Uncheck ‘Hide and show Front Row’
The final result looks like this:
Testing Getters and Setters Considered Useful
Posted: June 22, 2011 | Author: simeshev | Filed under: Software | Leave a comment »Writing unit tests for getters and setters is a good idea because such tests create a regression detection suite.
I sometimes hear the argument that setters and getters are not worth unit testing. The logic goes that as they don’t do anything, there is nothing to test. There is a couple of problems with this attitude:
- First problem: It uses proof by assertion (“Trust me, this method doesn’t do anything [special]”), which is impossible to verify using automated testing tools such as JUnit.
- Second problem: The behavior of a setter or a getter may expand in future (such as storing the property in a database), and when it happens, there won’t be a unit test to verify that methods still do what they are supposed to do.
Writing a unit test for setters and getters, as trivial as they are at the moment, creates a regression detection suite. This is important because if future changes to the method break it, the unit test will be there to catch the problem.
To make testing matching pairs of setters and getters easier, I usually test them in a single method testSetGet() instead of the pair testSet() and testGet():
Bean:
public class Bean {
private String property;
public String getProperty() {
return property;
}
public void setProperty(final String property) {
this.property = property;
}
}
Test method:
/**
* Tests setting and getting the property.
*/
public void testSetGetProperty() {
final String testValue = "Test value";
assertNull("Initial value should be null", bean.getProperty());
bean.setProperty(testValue);
assertEquals("Getter should return value set", testValue, bean.getProperty());
}
Test getters and setters and enjoy the benefits of the growing regression detection suite and the reliability of well-tested codebase.
Is intelligence gathered at Osama Bin Laden’s worth anything?
Posted: June 16, 2011 | Author: simeshev | Filed under: General | Leave a comment »Is it possible that a terrorist, known worldwide as being wanted dead or alive by the U.S. Government would keep top-secret and important documents at his hideout spot?
Let’s be serious here, Bin Laden was no fool; with most of the world searching for him and bounty rewards in the millions of dollars; Bin Laden knew he would eventually be caught.
Now the true question is if the documents found at his place of death were real or falsified. There is absolutely no way that Bin Laden would have kept such documents with him at all times. Documents with information on future attacks and how they would happen are targeted to a very limited amount of people.
The biggest reason that Bin Laden left the documents behind would be to confuse the U.S. government. This could be a very simple method to distract others from the actual targets.
The best way to deal with these documents would be to treat them with extreme suspicion and realize that someone who had such great power over so many people could not possibly have been that sloppy in his work. Does anyone really think that Bin Laden would have given the U.S. government advice on other terrorists?
Password Database for iPhone
Posted: February 17, 2011 | Author: simeshev | Filed under: Software | Leave a comment »Remembering passwords beyond a certain number maybe impossible and that’s where a password database can really help.
Over time we all acquire access rights to a bunch of online systems. Developer machines, production systems, version control, bug tracker, online banking, your home access point, Facebook, twitter, online publications – you name it. Sooner than later those accounts multiple to the point where it is pretty much impossible to remember them all.
Aside from writing passwords down and sticking them to your monitor, there are really two ways to manage passwords:
One way is to develop a system of deducing a password from the name of a website which is known to you only. For instance, get first and last letters of a website, attach your reverse birth date plus some (one) non-alphabetical charter. For instance, a password for this site would look like db0106!. No, this is *not* the password for this blog :-). The problem with this approach is that once this system is known, cracking the rest of your accounts is trivial. Also, there aren’t that many systems to come up with, and any system in a password makes it a subject of brute force attacks.
A much better approach is a secure password database. There are applications that can generate a random, system-less password for each of your accounts and that keep all your passwords in an encrypted database. The database is encrypted using a master password, and this is the only password that you need to remember. Without the master password the database is inaccessible. When you open such an application, it asks for the password and, once the password is verified, decrypts and displays the password database. Only then you can see all your passwords. The password database is better because all your passwords are impossible to guess, and all you need to remember is a single master password.
eWallet
Being an iPhone owner I use eWallet as a password database. There are other password applications but, to my taste, eWallet beats them all. It is convenient, intuitive and flexible. What’s cool is that if you are too lazy you can just photograph your credit cards and store images instead of entering all those numbers.